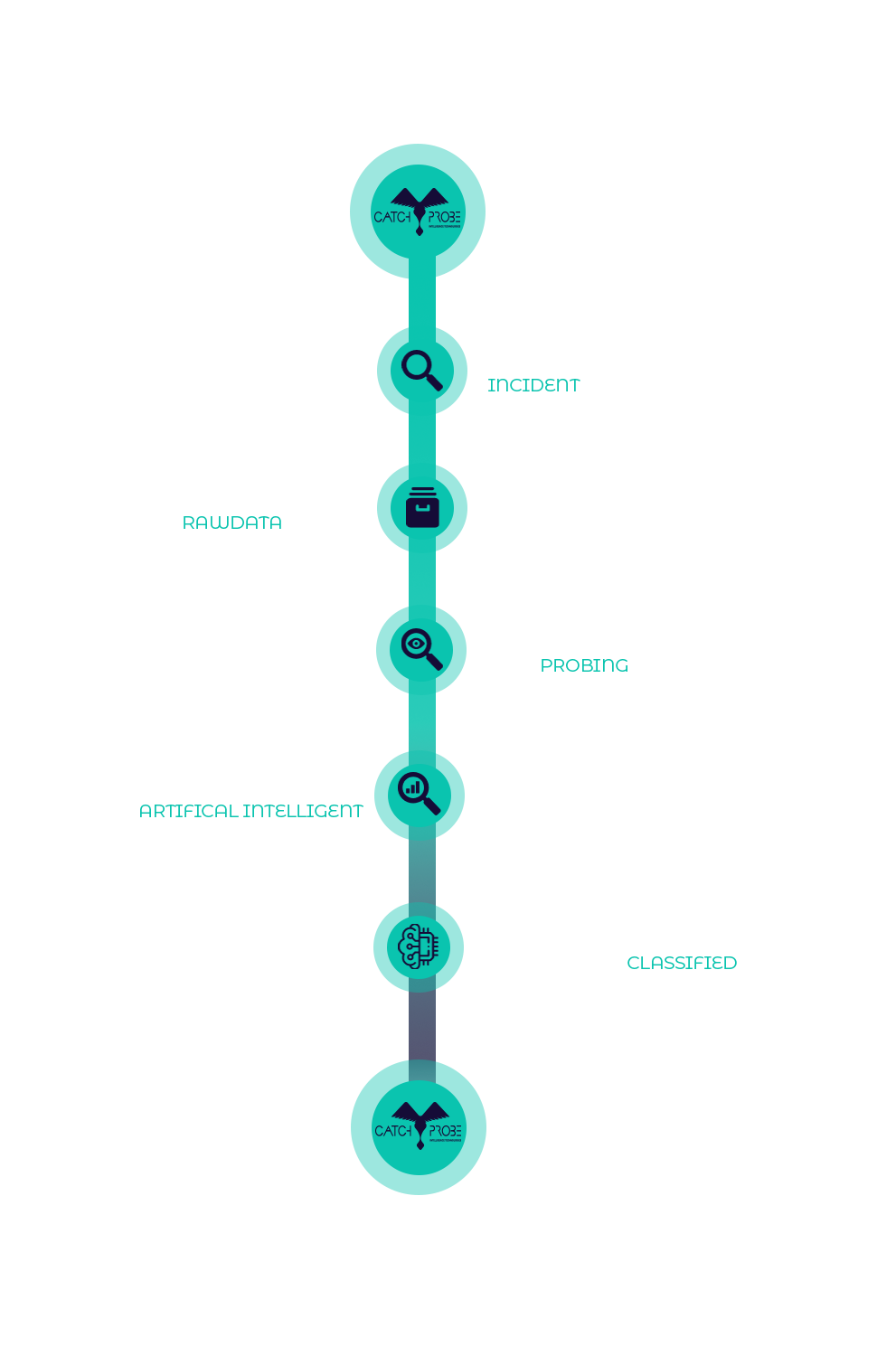
WHAT CATCHPROBE DOES FOR YOU
AI meets data
CAPABLE
CatchProbe gives you access to a variety of data sources, maps them, and profiles them for you.
Verifiable intelligence
DEPENDABLE
Stop getting overwhelmed by the amount of data others provide you. Get exactly what it is that you seek.
Proactive defense
ACTIONABLE
Have CatchProbe connect to your SIEM/Firewall to block threats and make further use of the verified intelligence.
Petabytes of Data and Prescience with
In-Depth Analysis and Actionable Intelligence
-
 STRUCTURAL ATTACK ANALYSIS
STRUCTURAL ATTACK ANALYSIS
-
 AUTONOMOUS INCIDENT RESPONSE with VERIFIED INTELLIGENCE
AUTONOMOUS INCIDENT RESPONSE with VERIFIED INTELLIGENCE
-
 BREACH DETECTION
BREACH DETECTION
-
 A SOURCE FOR LEAKED INFORMATION
A SOURCE FOR LEAKED INFORMATION
-
 MAPPING AND PROFILING
MAPPING AND PROFILING
-
 PROACTIVE WEB INTELLIGENCE
PROACTIVE WEB INTELLIGENCE

MAKES A DIFFERENCE WITH
CATCHPROBE MODULES
Enriching and making sense of collected intelligence data is among our priority objectives. We offer a detailed research and analysis platform created with analysts in mind. CatchProbe has developed multiple modules that expand the intelligence customers can collect, making additional resources available tailored to their needs. The platform makes it easy to collect and analyze the data you need to reach meaningful and actionable intelligence.


Empowering the Pursuit of Intelligence
A platform that is unlike any other. Covering your security needs, in one easy to use space.
ATTACKS AND ATTACKERS IS EASY WITH CATCHPROBE
Set your next generation artificial intelligence-based traps quickly and start making use of them right away. Going after attackers has never been simpler. Every attack against your traps captures and profiles the attackers’ information and provides it to you on your own dashboard.
Thousands of Threat Actors
GATHERING IS EASY WITH CATCHPROBE
CatchProbe provides different management features to companies and organizations that want to collect and analyze intelligence rich data. Data storage can be easily scaled horizontally thanks to micro service infrastructure, rather than being constrained by hardware limitations.
Undetectable

Actionable Intelligence Suite with
Centralized All-in-One SaaS Architecture
-
 SIMPLER
SIMPLER
-
 LESS COSTLY
LESS COSTLY
-
 FASTER WAY
FASTER WAY
-
 EASIER
EASIER
-
 MORE EFFECTIVE
MORE EFFECTIVE

Intelligence & Crime Fusion Center
Data Sheet
Our datasheets focus on serving the most essential information to answer initial questions about our products to help you with make informed buying decisions.

ThreatWay
Data Sheet
CatchProbe ThreatWay provides extensive threat intelligence collected from hundreds of sources and allows you to share the intelligence you want, when you need, inside and outside your organization.

SmartDeceptive
Data Sheet
Capture and gather information on new attack patterns and methods with CatchProbe’s NextGen AI-based deception system, SmartDeceptive.

DarkMap
Data Sheet